Which of the following network types provides the greatest security challenge, due to the diversity of end users, applications, and operating systems?
A) Medium-sized network
B) SOHO network
C) Enterprise network
D) Linux network
C) Enterprise network
You might also like to view...
The statements int x = 1; int y; y = --x;
a) Assign y the value 1; b) Change the value of x to 0 c) Assign to y the value 1; d) Assign to y the value 0; e) The -- is a prefix operator.
On switch SW3, what is the spanning tree information now? What is the STP path?
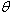
What will be an ideal response?
A. ?no-frills field B. ?nonkey field C. ?secondary field D. ?foreign field
Answer the following statements true (T) or false (F)
1. A computer is a complex system. 2. A computer organization does not need to be designed to implement a particular architectural specification. 3. Computer organization refers to attributes of a system visible to the programmer. 4. Changes in computer technology are finally slowing down.