Which of the following is a traditional Web page orientation?
A. landscape
B. square
C. portrait
D. default
Answer: C
You might also like to view...
The purpose of a_______ is to protect a LAN from intruders outside the network.
a) firewall. b) digital signature. c) restricted environment. d) None of the above.
What other actions should be taken?
What will be an ideal response?
Configure the network according to the specifications listed. Make sure that you address both the router and switch access rules. Test your network carefully, and then save your configuration. You will be asked to demonstrate your network to your instructor.
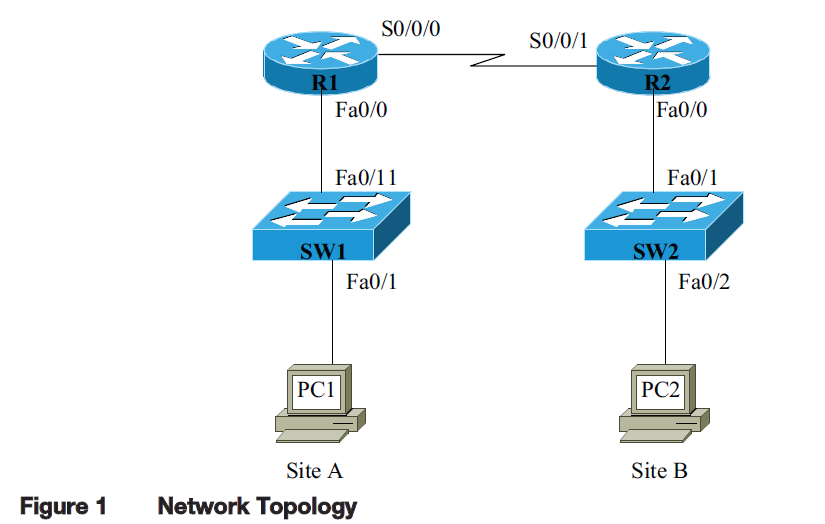
In this exercise, you are to configure NAT (Network Address Translation) for both networks (Site A
and Site B). The network topology for this network is provided in Figure 1. You are to use your
own IP addressing scheme.
Specifics
Router access rules:
? Only computers in Site A are allowed to configure R1.
? Only computers in Site B are allowed to configure R2.
? Access to routers is restricted to the use of the console port and Secure Shell (SSH) connection
(use Telnet if SSH is unavailable).
? All unused ports should be shut down.
? NAT must be used to map all private IPs to one public IP.
Switch access rules:
? Only computers in Site A are allowed to configure SW1.
? Only computers in Site B are allowed to configure SW2.
? Access to switches is restricted to the use of the console port and SSH connection (use Telnet if
SSH is unavailable).
You can undo a table property change by pressing the ____ keys.
A. CTRL+Z B. CTRL+P C. CTRL+S D. CTRL+X