Both the _______________ protocol and the newer, more secure _______________ protocol have been used to make HTTPS connections secure.
Fill in the blank(s) with the appropriate word(s).
Secure Sockets Layer (SSL); Transport Layer Security (TLS)
correct
You might also like to view...
Which of the following applications would a deque not be well suited for?
a. Applications that require frequent insertions and deletions at the front of a container. b. Applications that require frequent insertions and deletions in the middle of a container. c. Applications that require frequent insertions and deletions at the back of a container. d. Applications that require frequent insertions and deletions at the front and at the back of a container.
Identify the main idea behind the General Public License (GPL) and list three characteristics of software developed under the GPL.
What will be an ideal response?
Graph the point. ![]()
A. 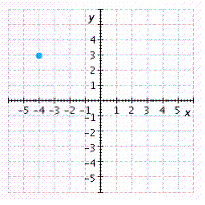
B. 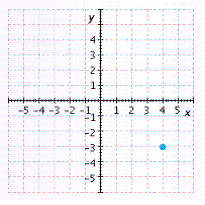
C. 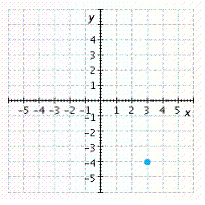
D. 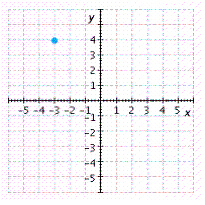
E. 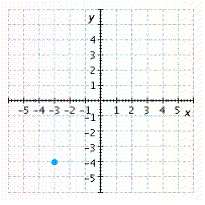
What makes a switch better than a hub?
A. A switch routes packets instead of frames to different networks. B. A switch divides bandwidth among connected devices C. A switch broadcast the data frames to every connected device D. A switch sends data frames to the correct connected device