Write a program that generates random numbers between 1 and 10 and fill an array of size 20 with them. Have your program sort the array then output in order the number of occurrences of each random number generated. Use the STL sort function to sort your array.
How to use the STL sort:
#include
...
int a[20]
...
sort(a,a+20);
Example Output:
This program generates random numbers and tabulates the results
Original List Sorted:
a[ 0] 1
a[ 1] 1
a[ 2] 1
a[ 3] 2
a[ 4] 2
a[ 5] 3
a[ 6] 6
a[ 7] 6
a[ 8] 6
a[ 9] 7
a[10] 8
a[11] 8
a[12] 8
a[13] 9
a[14] 9
a[15] 9
a[16] 9
a[17] 10
a[18] 10
a[19] 10
N Count
1: 3
2: 2
3: 1
4: 0
5: 0
6: 3
7: 1
8: 3
9: 4
10: 3
Try Again? (1 = yes, 0 = exit)
Answer:
C++ Program:
#include <iostream>
#include <algorithm>
#include <stdlib.h>
#include <time.h>
using namespace std;
int main()
{
int a[20];
int i, j, k=0, cnt=0;
int freq[10] = {0};
//Initializing random seed
srand (time(NULL));
//Generating random numbers
for(i=0; i<20; i++)
{
a[i] = (rand() % 10) + 1;
}
//Sorting array
sort(a, a+20);
//Printing sorted array
for(i=0; i<20; i++)
{
cout << "a[" << i << "] " << a[i] << endl;
}
//Number of occurrence of each number
for(i=1; i<=10; i++)
{
//Iterating over array
for(j=0; j<20; j++)
{
//Updating frequency
if(a[j]==i)
{
freq[i-1] += 1;
}
}
}
//Printing results
for(i=1; i<=10; i++)
{
cout << endl << i << ": " << freq[i-1];
}
cout << endl;
return 0;
}
______________________________________________________________________________________________________
Sample Run:
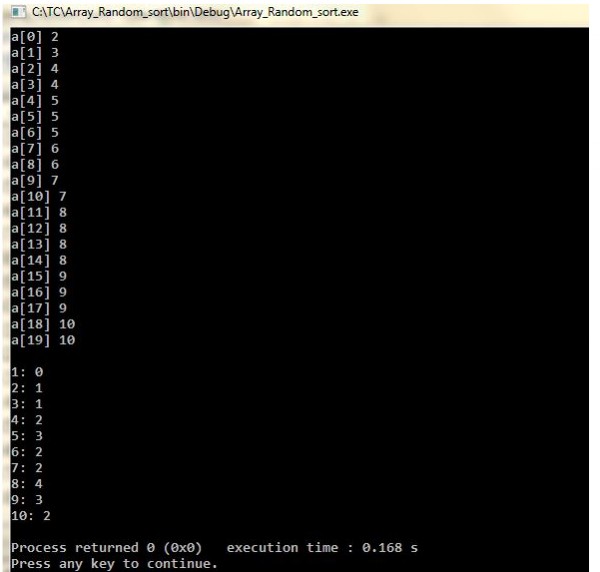
You might also like to view...
What is an advantage of the anomaly detection method?
A. makes use of signatures of well-known attacks B. system can detect attacks from inside the network by people with stolen accounts C. easy to understand and less difficult to configure than a signature-based system D. after installation, the IDPS is trained for several days or weeks
Which type of memory is non-volatile?
A) DDR2 B) RAM C) SDRAM D) ROM
It is possible to use calculations to update a value in a column.
Answer the following statement true (T) or false (F)
An administrator notes that after a recent power outage, some open files were corrupted on one affected file server. Which of the following items should the administrator consider to determine the cause of this corruption?
A. The servers memory B. The servers RAID controller battery C. The servers processor D. The servers NIC teaming configuration