The ________ function looks up values in a table array arranged as vertical columns
Fill in the blank(s) with correct word
VLOOKUP
You might also like to view...
What is the terminating condition and stopping case of the fibonacci function?
What will be an ideal response?
The __________ attack is where the attacker chooses a list of messages before attempting to break the user's signature scheme, independent of the user's public key. The attacker then obtains from the user valid signatures for the chosen messages.
Fill in the blank(s) with the appropriate word(s).
When a parameter is declared using the __________ qualifier, the procedure has access to the original argument variable and may make changes to its value.
a. ByValue b. ByAddress c. ByRef d. ByDefault
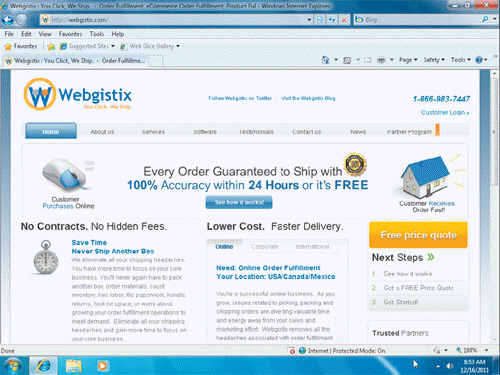 Webgistix, shown in the accompanying figure, is an example of a(n) _________________________ or fulfillment house.
Webgistix, shown in the accompanying figure, is an example of a(n) _________________________ or fulfillment house.
Fill in the blank(s) with the appropriate word(s).