Which of the following is used to move copy to the next column?
A. Section Break
B. Continuous Section Break
C. Column Break
D. Page Break
Answer: C
Computer Science & Information Technology
You might also like to view...
Kerberos relies exclusively on __________ .
A. symmetric encryption B. asymmetric encryption C. private key encryption D. public key encryption
Computer Science & Information Technology
This OSI layer ensures error-free packets.
What will be an ideal response?
Computer Science & Information Technology
Put the following equations into the slop-intercept form (y = + b) and read the value of the slope and y-intercept.
y = 3x + 2 Already in standard form Slope = +3
Computer Science & Information Technology
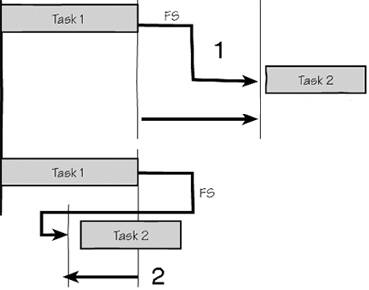 The time marked 2 in the accompanying figure is called ____ time.
The time marked 2 in the accompanying figure is called ____ time.
A. lead time B. negative lag time C. both a and b D. none of the above
Computer Science & Information Technology