What do audit logs that track user activity on an information system provide?
A. identification
B. authorization
C. accountability
D. authentication
Answer: C
You might also like to view...
Which of the following does a binary tree have?
a) A root node b) Links that point back to its predecessor in the tree. c) Inaccessible nodes d) A leaf node or nodes e) Null pointers on the leaf links f) Exactly two links at each node.
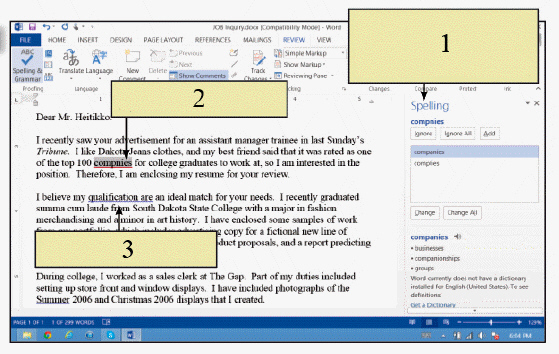 In the accompanying figure, the word referenced by item 3 has been ____.
In the accompanying figure, the word referenced by item 3 has been ____.
A. replaced by the thesaurus B. flagged by the grammar checker C. missed by the grammar and spelling checker D. flagged by the spelling checker
What is the Session menu? When and where does it appear? How do you use it?
What will be an ideal response?
Thetypevalue ____ for theinputelement causes most browsers to display text entered by users as bullets or asterisks rather than showing the actual characters.
A. password B. hide C. secure D. username