You can save Performance Monitor charts as image files, so that you can review them for later reference
Indicate whether the statement is true or false
TRUE
You might also like to view...
Which IDPS customization option is a list of entities known to be harmless?
A. thresholds B. whitelists C. blacklists D. alert settings
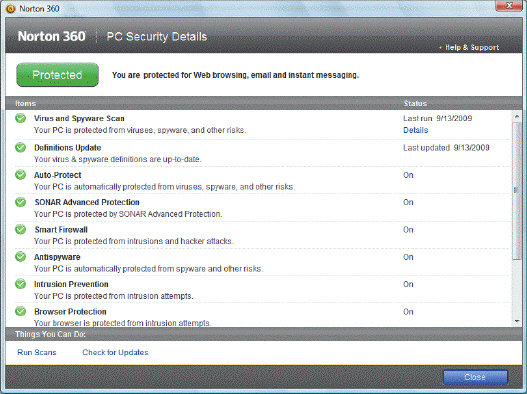 The application shown in the accompanying figure is an example of a(n) ____.
The application shown in the accompanying figure is an example of a(n) ____.
A. firewall B. Trojan horse C. encryption program D. security suite
Case-Based Critical Thinking Questions ? Case 7-1 Ted knows that macros can be helpful to him in his work with Excel spreadsheets, but he also knows they have their hazards, so he comes to you for guidance about what kind of security settings he should put in place, and at what times. ? ? As Ted does more even work in Excel, he has begun to develop a collection of publishers whom he trusts to deliver macros that are problem-free. What should his option be in the Trust Center?
A. Enable all trusted macros B. Enable all macros C. Disable all macros except digitally signed macros D. Disable a macro with notification
To create a form, use the Form button or the Form dialog box. ____________________
Answer the following statement true (T) or false (F)