Applying a three-dimensional frame to an image using shadows is called ____.
A. beveling
B. resampling
C. layering
D. cropping
Answer: A
You might also like to view...
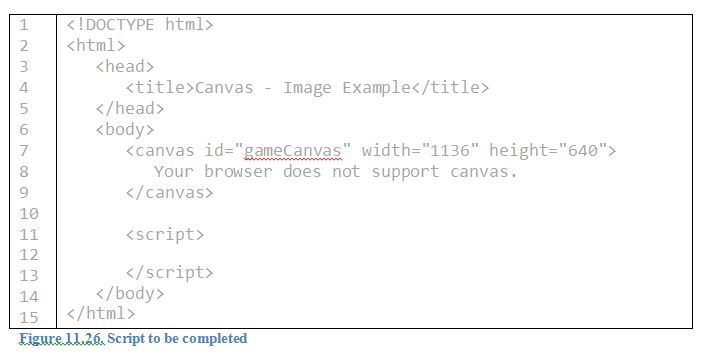
Place the following statements (a) - (d) in the correct order in line 12 of the code shown in Figure 11.26 so that a tree image will be displayed on the canvas.
a. myContext.drawImage(obstacle, 250, 70);
b. var myCanvas = document.getElementById("gameCanvas");
var myContext = myCanvas.getContext("2d");
c. obstacle.src = "images/tree.png";
d. var obstacle = new Image();
Metrics that are useful for profile-based intrusion detection are: counter, gauge, resource utilization, and _________ .
Fill in the blank(s) with the appropriate word(s).
The _______ states that bits can represent all discrete information even though the bits have no meaning of their own.
Fill in the blank(s) with the appropriate word(s).
Create a PL/SQL procedure object in your schema. Using a Cursor the procedure code should be able to retrieve records of all employees and check in which city they live. If an employee lives in Glasgow the procedure should insert a record in the table GlasgowEmployees.
Assume that the following tables are part of a Library database system Employee(empNo, fName, lName, street, city, sex, salary, libName) GlasgowEmployees(gEmpNo, fName, lName, sex, salary)