Security by obscurity is sometimes criticized as being too weak.
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
With the Posterize effect set to four, each pixel in the image can be one-and only one-of four available shades of gray.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The ________ pane can be used to hide components of a slide that you do not want to see but do not want to delete
A) Format Shape B) Selection C) Clipboard D) Slide
Computer Science & Information Technology
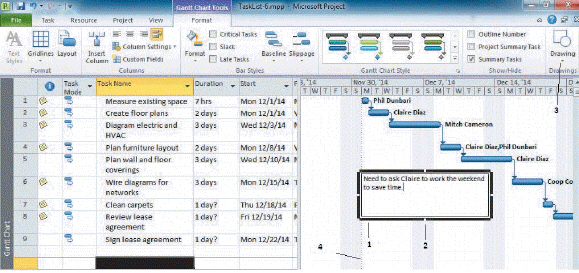 The small white rectangle marked 2 in the accompanying figure is called a ____ handle.
The small white rectangle marked 2 in the accompanying figure is called a ____ handle.
A. embedded B. text C. modification D. sizing
Computer Science & Information Technology
What is the problem with demanding perfection?
What will be an ideal response?
Computer Science & Information Technology