Twitter currently has more than 500 million users who generate more than ________ million tweets each day
Fill in the blank(s) with correct word
340
You might also like to view...
Configure the network according to the specifications listed. Make sure that you address both the router and switch access rules. Test your network carefully and then save your configuration.
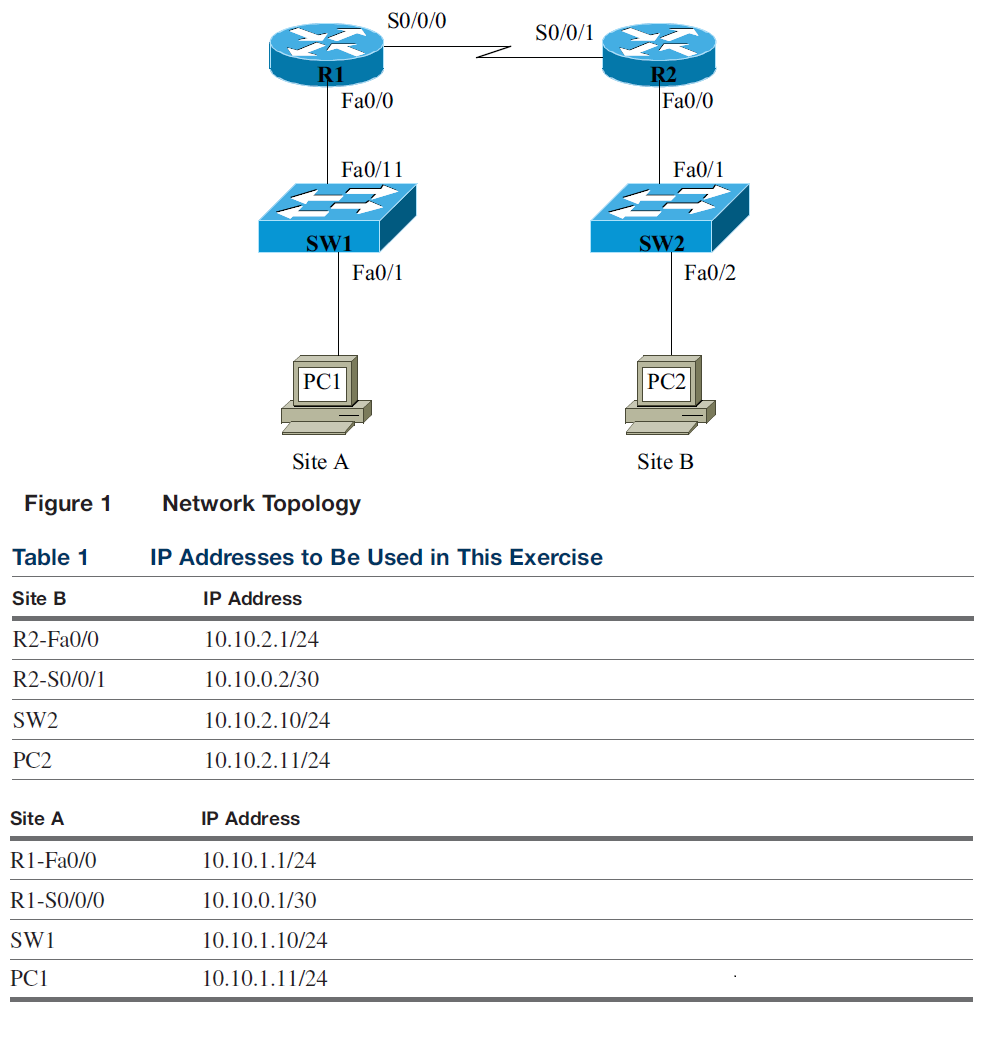
Specifics
Router access rules:
? Only computers in Site A are allowed to configure R1.
? Only computers in Site B are allowed to configure R2.
? Access to routers is restricted to use of the console port and Secure Shell (SSH) (use Telnet if
SSH is unavailable).
? All unused ports should be shut down.
Switch access rules:
? Only computers in Site A are allowed to configure SW1.
? Only computers in Site B are allowed to configure SW2.
? Access to switches is restricted to use of the console port and SSH (use Telnet if SSH is
unavailable).
? Use MAC address–based port security to ensure that only authorized devices can communicate.
? All unused ports should be shut down.
Color ____ changes the intensity of colors.
A. tone B. density C. saturation D. brightness
What is an incremental backup?
What will be an ideal response?
Define an edge router, including both its role and the larger system within which it exists.
What will be an ideal response?