The security triad consists of confidentiality, nonrepudiation, and availability
Indicate whether the statement is true or false.
ANS: False: The security triad consists of confidentiality, integrity, and availability.
You might also like to view...
The following is a summary of the required tasks that are to be completed in this exercise:
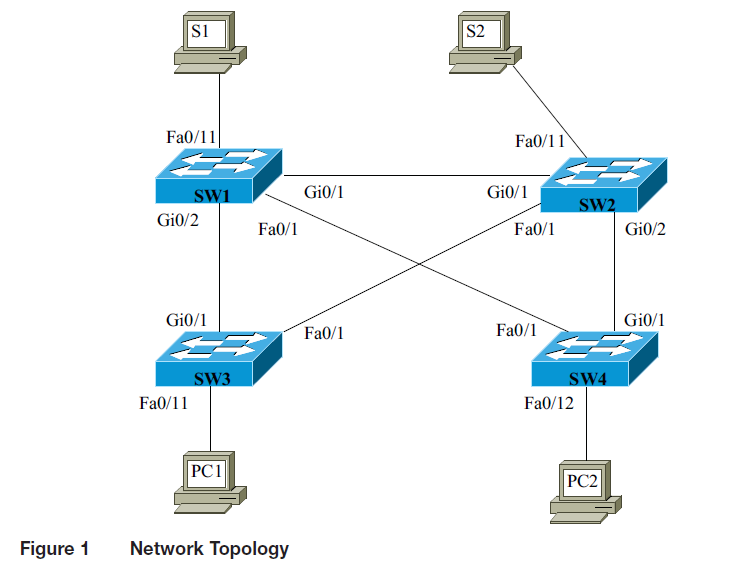
The objective of this project is to examine the student’s ability to configure VLANs using the
VLAN Trunking Protocol (VTP). VTP domain and passwords are up to the student. This network
setup uses four switches, with no redundant links. The network topology for this lab is provided in
Figure 1. The specific IP addresses are up to the student; however, they must be configured for
operation in the specified networks.
Specifics
? VLAN 10, Office: PC1, S2
? VLAN 20, Finance: PC2, S1
? Network: 192.168.10.0/24, 192.168.20.0/24
Disabled redundant ports:
? SW1(fa0/1), SW2(fa0/1), SW3(fa0/1), SW4(fa0/1)
VTP:
? VTP Server: SW1
? VTP Transparent: SW4
? VTP Clients: SW2, SW3
Required
1. Configure the network according to the specifications listed.
2. Disable the interfaces on any redundant links.
3. Configure the VTP server, clients, and transparent switch.
4. Add the VLANs to
In VBA, the ________ operator requires that any one of the conditions evaluate to True
A) Not B) Or C) And D) But
A security analyst receives an alert from a WAF with the following payload: var data= “
A. Cross-site request forgery B. Buffer overflow C. SQL injection D. JavaScript data insertion E. Firewall evasion script
How does the nice value affect process priority? How and why can nice values be altered?
What will be an ideal response?