With an overlay system, each geographic region has its own area code.
a. True
b. False
b. False
You might also like to view...
Show that the FIFO-ordered multicast algorithm does not work for overlapping groups, by considering two messages sent from the same source to two overlapping groups, and considering a process in the intersection of those groups. Adapt the protocol to work for this case. Hint: processes should include with their messages the latest sequence numbers of messages sent to all groups.
What will be an ideal response?
(Enhanced Bank Account Information Application) Modify below to enable the user to input both a withdrawal amount and a deposit amount (Fig. 4.16). When the Enter JButton is clicked, the balance is updated appropriately.
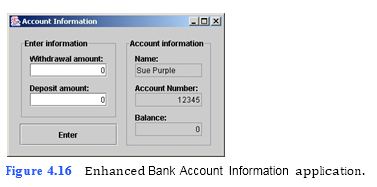
a) Copying the template to your working directory. Copy the C:Examples Tutorial04ExercisesAccountInformationEnhancement directory to your C:SimplyJava directory.
b) Opening the Command Prompt window and changing directories. Open the Com- mand Prompt window by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJava AccountInformationEnhancement.
c) Compiling the template application. Compile your application by typing javac
AccountInformation.java. JTextField, then press the Enter JButton. The Balance: JTextField should now contain 100, and the Deposit amount: JTextField should now contain 0.
d) Running the template application. Run the enhanced Bank Account Information template application by typing java AccountInformation. Type 50 in the With- drawal amount: JTextField and type 100 in the Deposit amount: JTextField. When you press the Enter JButton, notice that the balance does not
In a network configured with a ________ topology, the nodes are all connected using a single cable that is terminated on both ends
A) bus B) ring C) hybrid D) star
Most crypto-malware propagates via a Trojan horse.
Answer the following statement true (T) or false (F)