The process by which attackers change the format and/or timing of their activities to avoid being detected by the IDPS is known as a false attack stimulus.
Answer the following statement true (T) or false (F)
False
You might also like to view...
The command outFile.width(10) is used to
a. change the number of characters in the output b. sets the filename of outFile to 10 characters c. always uses 10 characters to display the output d. displays the next value in at least 10 characters
The intermediate Stream operation ________ results in a stream containing only the elements that satisfy a condition.
a. distinct b. map c. filter d. limit
Show how a browser would render the following code:
- item one
- item three
- item two
In this lab, you are configuring OSPF to the adjacent LAN for the network shown in Figure 1. You will be required to verify that computers in your LAN can ping the neighbor LAN. Note that a serial interface is being used to interconnect the LANs. You are configuring routing for both 172.20.15.0 and 192.168.25.0 networks. A subnet mask of 255.255.255.224 is being used. Use 56000 for the clock rate on the serial link (DCE interface). Use a subnet mask of 255.255.255.252 on the serial link connecting the two routers.
Computer IP Addresses, Subnet Masks, and Gateway Addresses
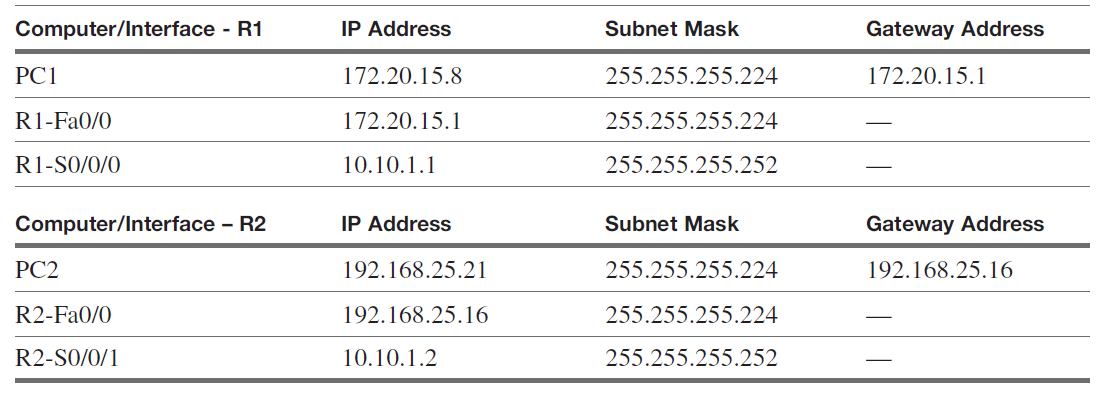
1. Configure the gateway address for FastEthernet 0/0 and the serial s0/0/0 interfaces on
Router R1. You also need to configure the IP address and the gateway address for PC-1.
Use the IP address and subnet mask specified in Table 1. You will need to enable each
interface and set the clock rate on the serial interface to 56000. List the router prompts
and commands used to configure the interfaces.
2. Configure the gateway address for FastEthernet 0/0 and the serial s0/0/1 interfaces on Router R2. Use the IP addresses and subnet masks specified in Table 1. Enable each interface and list the router prompts and commands used to configure the interfaces.
3. Configure the host name for your routers. R1 should be renamed LAN-A, and R2 should be renamed LAN-B. List the router prompts and commands used to configure the router’s host name.
4. The proper commands to verify that the interfaces on the LAN-A and LAN-B routers have b