The recent wave of network attacks that have hit companies such as eBay and Yahoo are known as ________.
Fill in the blank(s) with the appropriate word(s).
distributed denial-of-service attacks.
You might also like to view...
Consider the figure given below. When you request a network activity-such as printing a document using a network printer-the application program first passes the job to the _____.
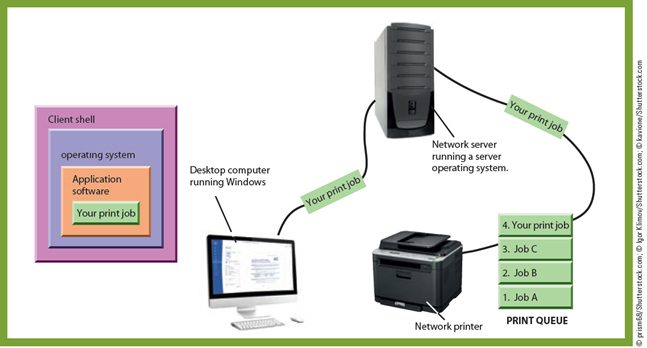
A. ?desktop operating system B. ?network operating system C. ?server operating system D. ?embedded operating system
?Any style that is applied to thethead, tbody,ortfootelement is _________ by the rows those elements contain.
Fill in the blank(s) with the appropriate word(s).
Which of the following is the path to the Error Checking button?
A. (AUDITING tab | Formulas group) B. (FORMULAS tab | Error Checking group) C. (FORMULAS tab | Formula Auditing group) D. (ERROR CHECKING tab | Watch Cells group)
____ was designed by IBM in the 1970s and is the most widely used symmetric cipher.
A. RC4 B. RC5 C. DES D. AES