In addition to deauthenticate messages, an attacker could flood wireless clients with ________.
RTS
CTS
Both RTS and CTS
Neither RTS nor CTS
Both RTS and CTS
Computer Science & Information Technology
You might also like to view...
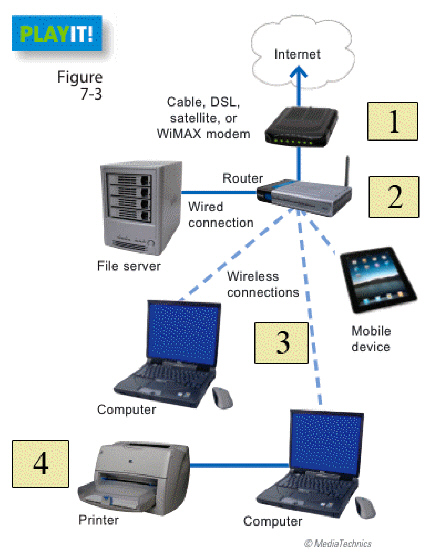 In the figure above, which item represents the device used to connect to the Internet?
In the figure above, which item represents the device used to connect to the Internet?
A. item 2 B. item 5 C. item 1 D. item 3
Computer Science & Information Technology
Determines the space between controls in a report or form
a. Control area b. Spacing c. Padding
Computer Science & Information Technology
Toolbox objects unique to Web application objects include Navigation objects for allowing user access.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Which of the following is NOT a citation style??
A. ?MLA B. ?ACA C. ?APA D. ?Chicago
Computer Science & Information Technology