A(n) ______ demands payment to stop an attack.
A. hacker
B. cracker
C. script kiddie
D. cyberextortionist
Answer: D
You might also like to view...
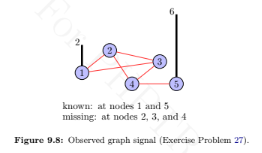
This problem demonstrates the use of Laplacian quadratic form for interpolation on graphs. Consider an observed graph signal, shown in Figure 9.8, where signal values at nodes 2, 3, and 4 are missing. The aim of interpolation is to fill in the missing values. One criteria for estimating the missing values is to minimize the squared sum of the differences in signal values between the neighboring vertices, which is nothing but the quadratic form of the graph Laplacian. Therefore, the interpolation problem can be written as
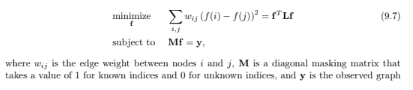
signal with zeros at missing indices. For example, if the values at nodes 2, 3, and 4 are
missing, the masking matrix is
M = diag {1,0,0,0,1} and the observed graph signal can be
written as y = [2, 0, 0, 0, 6] T. Find the missing values in the observed graph signal by solving
the above optimization problem. Hint: Use the method of Lagrange multipliers.
Create an initial ERD for the new system that contains at least eight entities.
What will be an ideal response?
You can define a bleed area when you create a document or at any time after it has been created.
Answer the following statement true (T) or false (F)
Answer the following statements true (T) or false (F)
1. CASE tools promote code reusability but do not help increase programmer productivity. 2. If the transaction record key is greater than the master record key then the next transaction record is read and processed against the current master record. 3. An error will occur if an attempt is made to add a transaction record to a master file and the record already exists in the master file. 4. An error will occur if an attempt is made to add a transaction record that has the same key field value(s) as a master record that has just been deleted from the master file. 5. If the transaction record key is less than the master record key then the transaction record is added to the master file and a new master file record is read.