What are the advantages and disadvantages of using a peer-to-peer system?
What will be an ideal response?
Answers will vary.
Computer Science & Information Technology
You might also like to view...
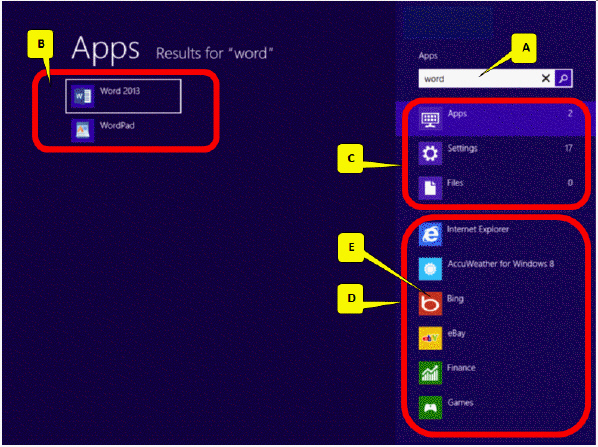 The accompanying figure illustrates the screen that appears when you type "word" in the text box. Which of the following is the title of this screen that is missing in this picture?
The accompanying figure illustrates the screen that appears when you type "word" in the text box. Which of the following is the title of this screen that is missing in this picture?
A. Search B. Start C. Programs D. Select
Computer Science & Information Technology
Explain how granular locking can be used at the SERIALIZABLE isolation level.
What will be an ideal response?
Computer Science & Information Technology
By using a PivotTable, you can show the same data in a table in ________
A) a summarized fashion B) large amount of cells C) field names D) more than one arrangement
Computer Science & Information Technology
What two types of attacks are VoIP call managers and VoIP phones most likely to be susceptible to?
A. DoS and malware B. Worms and Trojans C. DoS and host OS attacks D. Host OS attacks and buffer overflows
Computer Science & Information Technology