A ____ is a computer that uses a browser to request information from a Web server.
A. server
B. browser
C. middle-man
D. client computer
Answer: D
Computer Science & Information Technology
You might also like to view...
An ideal hash algorithm will require a cryptanalytic effort __________ the brute-force effort.
A. less than or equal to B. greater than or equal to C. less than D. greater than
Computer Science & Information Technology
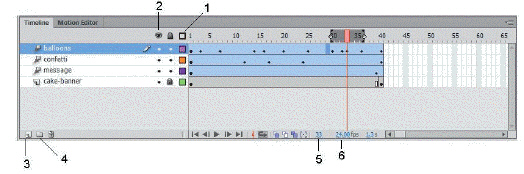 The item marked ____ in the accompanying figure is the Show All Layers as Outlines icon.
The item marked ____ in the accompanying figure is the Show All Layers as Outlines icon.
A. 1 B. 3 C. 5 D. 6
Computer Science & Information Technology
Review the sound settings available via the Effect list in the Property inspector and the ways in which each effect modifies the way a sound plays.
What will be an ideal response?
Computer Science & Information Technology
Protected Mode is enabled by default on all Internet zones
Indicate whether the statement is true or false
Computer Science & Information Technology