A graphic representation of numeric data is called a(n) ________
Fill in the blank(s) with correct word
chart
You might also like to view...
Describe how the retransmission timeout (RTO) value is determined in TCP.
What will be an ideal response?
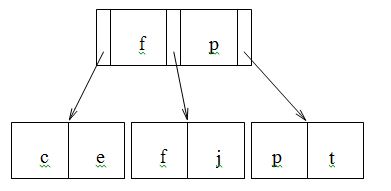
Search key value s is to be inserted in the following B+ tree. Show what the tree looks like after the insertion.
When ________ is selected, you can change one dimension of the table and the other dimension will automatically be changed to maintain the proportion
A) lock aspect ratio B) section C) merge D) AutoFit
Dave is responsible for password security in his organization and would like to strengthen the security of password files. He would like to defend his organization against the use of rainbow tables. Which one of the following techniques is specifically designed to frustrate the use of rainbow tables?
A. Password expiration policies B. Salting C. User education D. Password complexity policies